SIEM as the backbone to organizational cybersecurity
Typically, in enterprise networks many methods are used to prevent issues, such as, firewalls, anti viruses, and even more robust security solutions. While the market leaders in this industry will help prevent most of the modern cybersecurity threats, they all at some point fail.
It is at this point that the cybersecurity investigative research phase commences centered around four key areas:
- Detection – The ability to, in real-time, become aware
that an incident has taken place. - Containment – After the threat is identified, be able to
minimize its impact into other dependent systems. - Persecution – Pinpoint the culprit that provoked the incident.
- Remediation – Be able to document the incident, based on accurate data, plot a set of action and inform stakeholders in order to prevent similar incidents from re-occurrence.
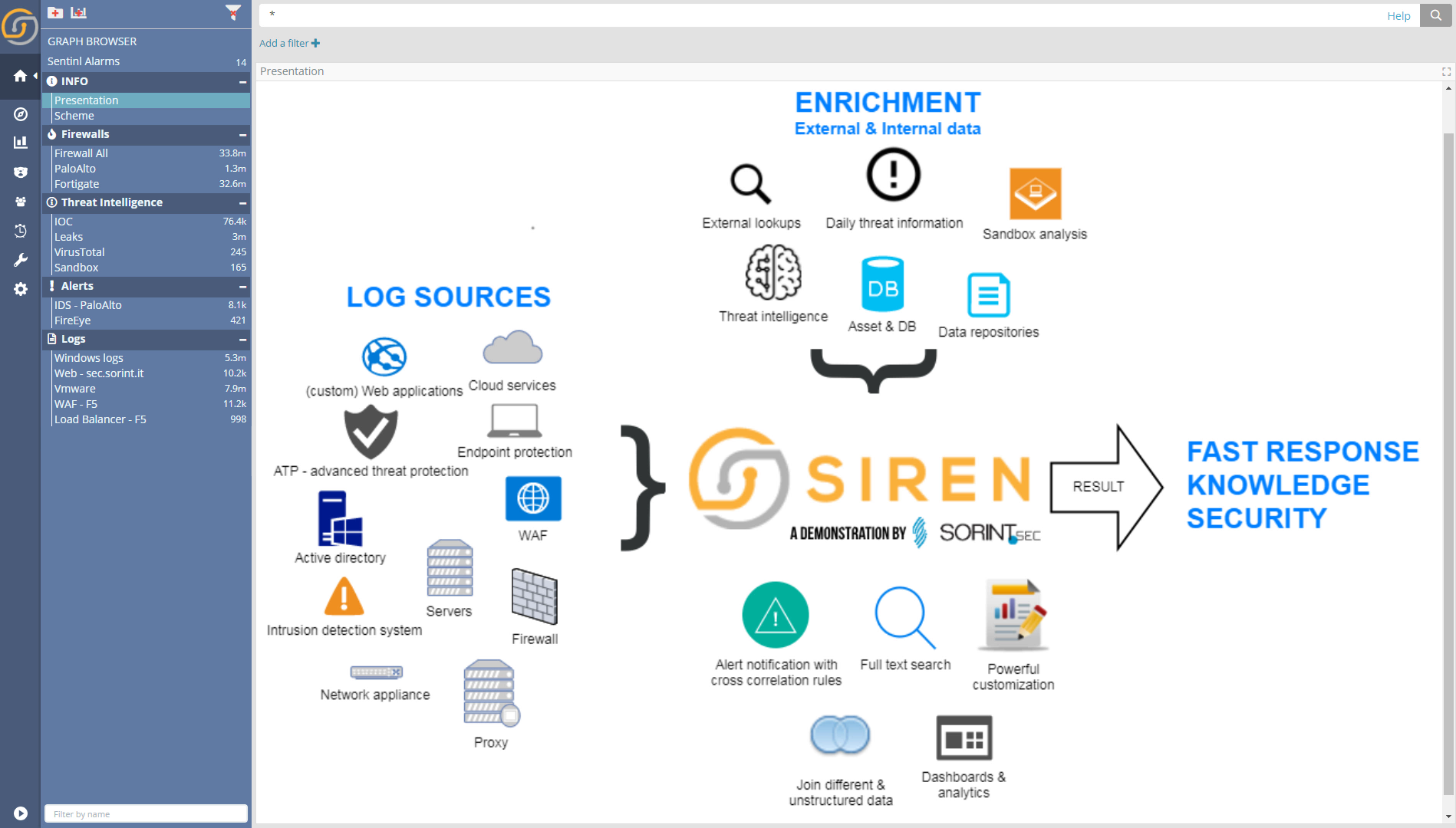
Supercharging ELK for cybersecurity
Elasticsearch is an outstanding storage for security related logs. With its ability to scale, search and drill down, it provides a great basis for investigation.
The Siren Federate plugin for Elasticsearch augments these great base capabilities with cross index/cross back end analysis and correlation (joins). These are critical capabilities in cyber security as the analyst can ‘join the dots’ at scale, across indexes and JDBC systems answering questions such as: ‘are there any records on the Fortinet index, where the destination IP is equal to the source IP on the PaloAlto index?’
In the screenshot below, the Siren installation described in this use case; dozens of cybersecurity related log are loaded and are accessible clicking the individual dashboard titles (left sidebar).
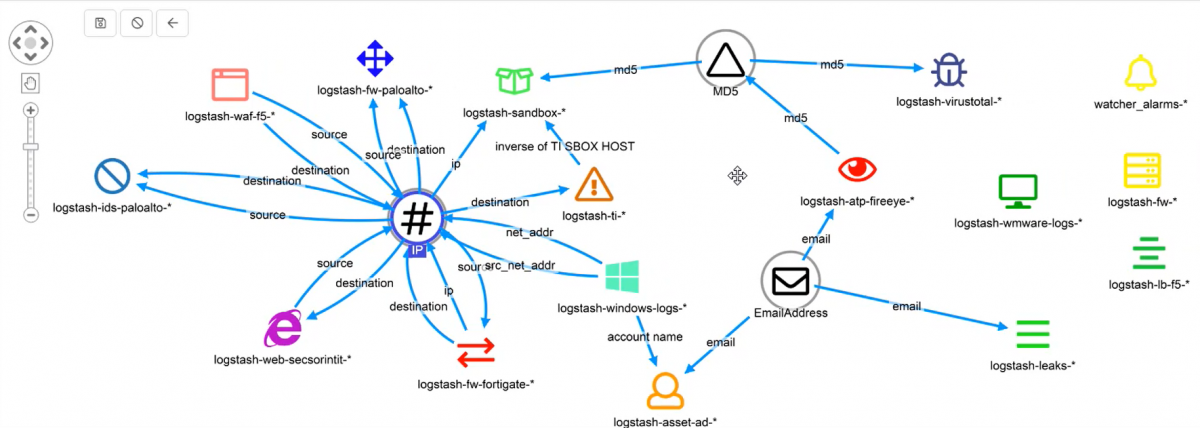
At the heart of cross index correlation – the Siren data model
At the heart of Siren’s ability to show relations between indexes, lies the Siren relational data model. Indexes, which can be either on Elasticsearch proper or directly in JDBC datasources, are connected to one another via properties like “source”, and “destination” to concepts, like “IP”, “MD5s” or “UserIDs”.
The combined relationships across entities allows the user interface to show relational filter buttons that enable cross-index and cross back-end record correlations, at scale.
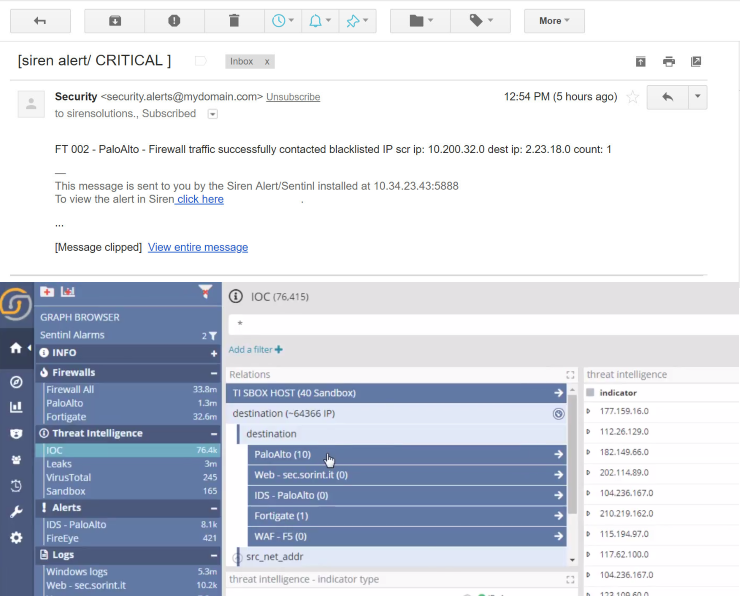
Blacklisted traffic use case
Alert: traffic to IOC IP
The use case begins with an analyst receiving an email from Siren Alert informing him/her of an ongoing potentially hazardous real-time event.
Following the link one reaches the respective IOC dashboard within the Siren Investigate UI, where the analyst can see how man IOCs are relationally connected with records in various other indexes. It is therefore simple to identify, for example, records in the PaloAlto index in which the destination IP address matches the one seen in the IOCs.
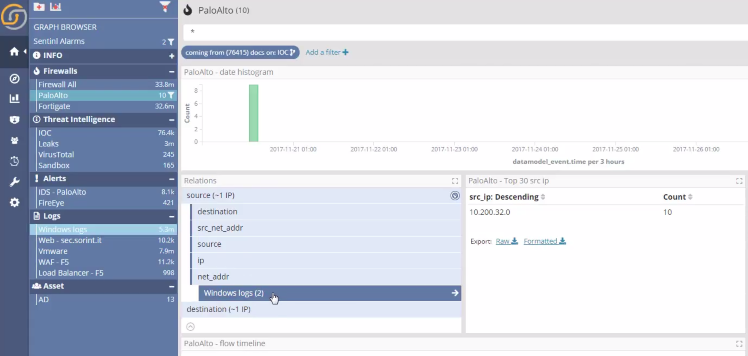
By pivoting relationally from the IOC dashboard to the PaloAlto index dashboard, we can then see what was the internal address of the host, and from there join them with the Windows logs…
…to then reach the Active Directory index, which is filtered to find the the user who is potentially compromised.
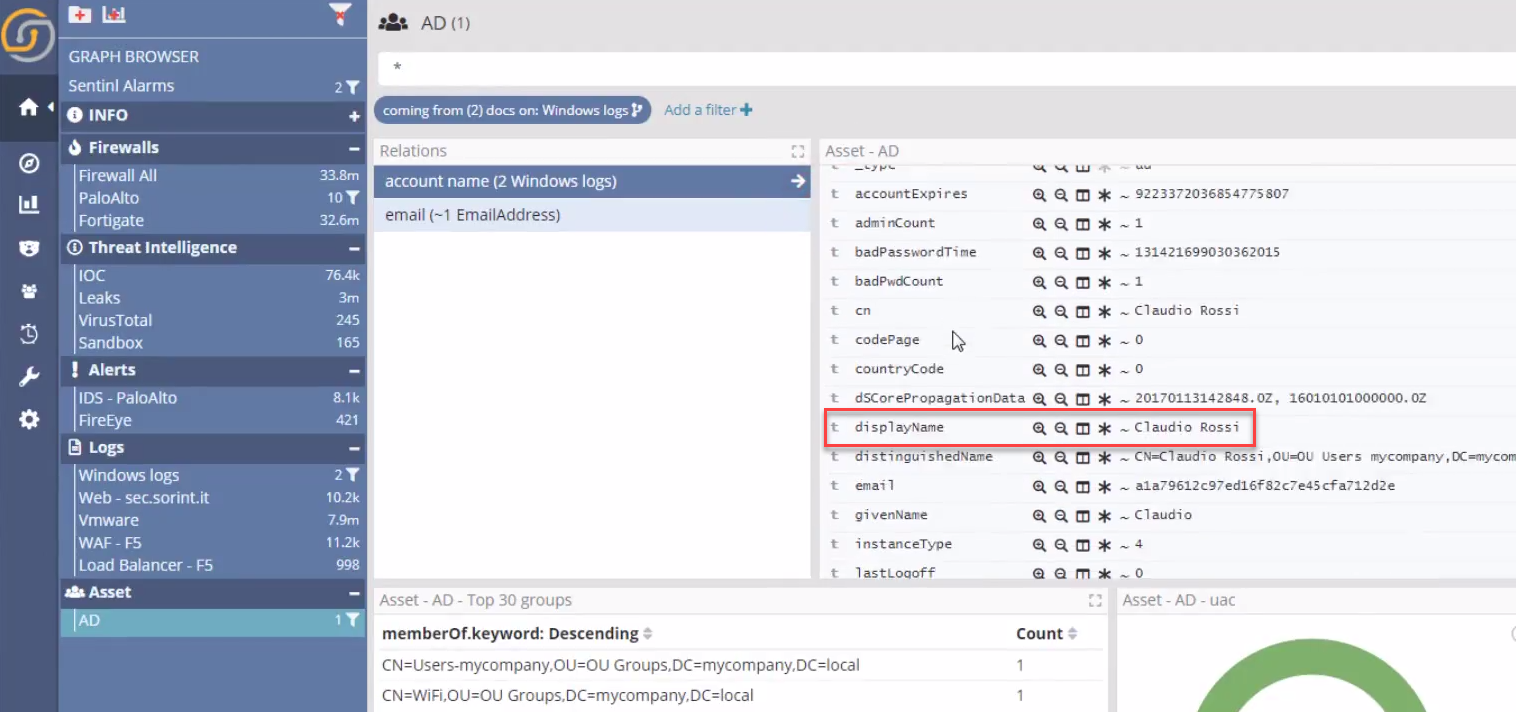
A single investigative view
At any time, Siren offers the ability to project the current dashboard records into a visual link analysis mode, to understand the incident as a whole, via single interactive layer to investigate further.
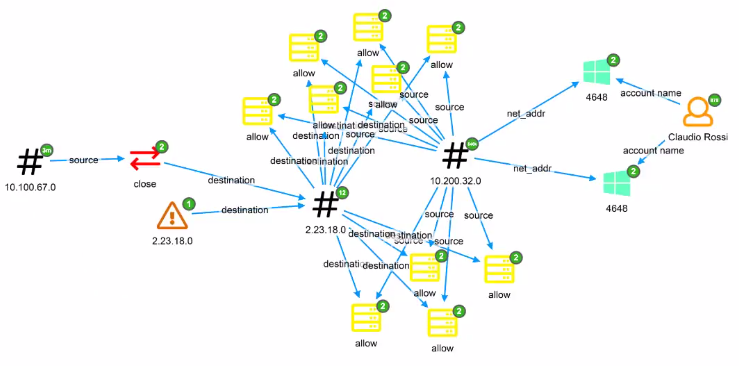
The Siren graph browser is a state-of-the-art, fully scriptable, with big data aggregate support link analysis tool which enables the user to explore their data through relations and entities intuitively, much in the way a user actually thinks.
Empowered by the Siren data model, the user can add the previously filtered records and can visually explore the connections to other events and records across systems. Having found a number of extra events, the user can pivot to the appropriate dashboard as needed to view the details.
Scenario study summary
Elasticsearch is a very popular choice for Security Information Event Management (SIEM) applications. With its ability to scale horizontally it can handle enormous amounts of real time logs, and its a natural way to store (and search) the tons of logs that network appliances and security products produce.
But while basic searching and aggregating are prerequisites, in Cybersecurity it is essential to join the dots and investigate across logs and across different backend system.
Siren can connect to existing Elasticsearch deployments and provide:
- Relational capabilities to correlate records at scale across indexes and across backends
- Enterprise grade access control and alerting which can make use of cross index / cross backend join conditions
- Record to record graph investigation: explore, expand relationships and pivot directly back to the corresponding dashboard for full result details.
Watch it in action
The use case above, in more details, in the video below.



