Note: Available only to qualifying organizations

The whole analysis is driven by named entity extraction, which finds find connections, locations, and topics associated with those entities.
Entities that are extracted, cleaned and consolidated to form centers of aggregations include phone numbers, social media handles, email addresses, and usernames.
The ability to lawfully analyze data coming from mobile phones that have been seized is an absolute necessity for Law Enforcement agencies worldwide, which rely on these for solving cases on a weekly basis.
Specialized software and hardware exist – possibly the most famous of which is Cellebrite – that extract and give visibility on mobile device data, such as retrieving contacts and reconstructing a timeline of calls.
Siren is now capable of taking data files from these “physical extractors” and allows investigators to search and analyze them. augmenting the data that is already present in Siren.
Here is an example of what the investigator sees, using sample anonymized data:
Siren for mobile device data: Enabling now what wasn’t possible before
Given that systems exist to view mobile device data, such as Cellebrite’s own Pathfinder, what is it that Siren offers that was not previously possible?
Two things.
Firstly, it offers instant connectivity between the device data and every other piece of data available to the investigative agency.
As opposed to simply searching and analyzing data that comes from the device, a Siren deployment can find a connection between any identifier on the phone (e.g. phone numbers, contact names, email addresses) and every identifier that may already be known in databases and datasets of the agency.
Example: What is the shortest path between a LOCATION where a bombing has taken place and a device that was seized in a raid?
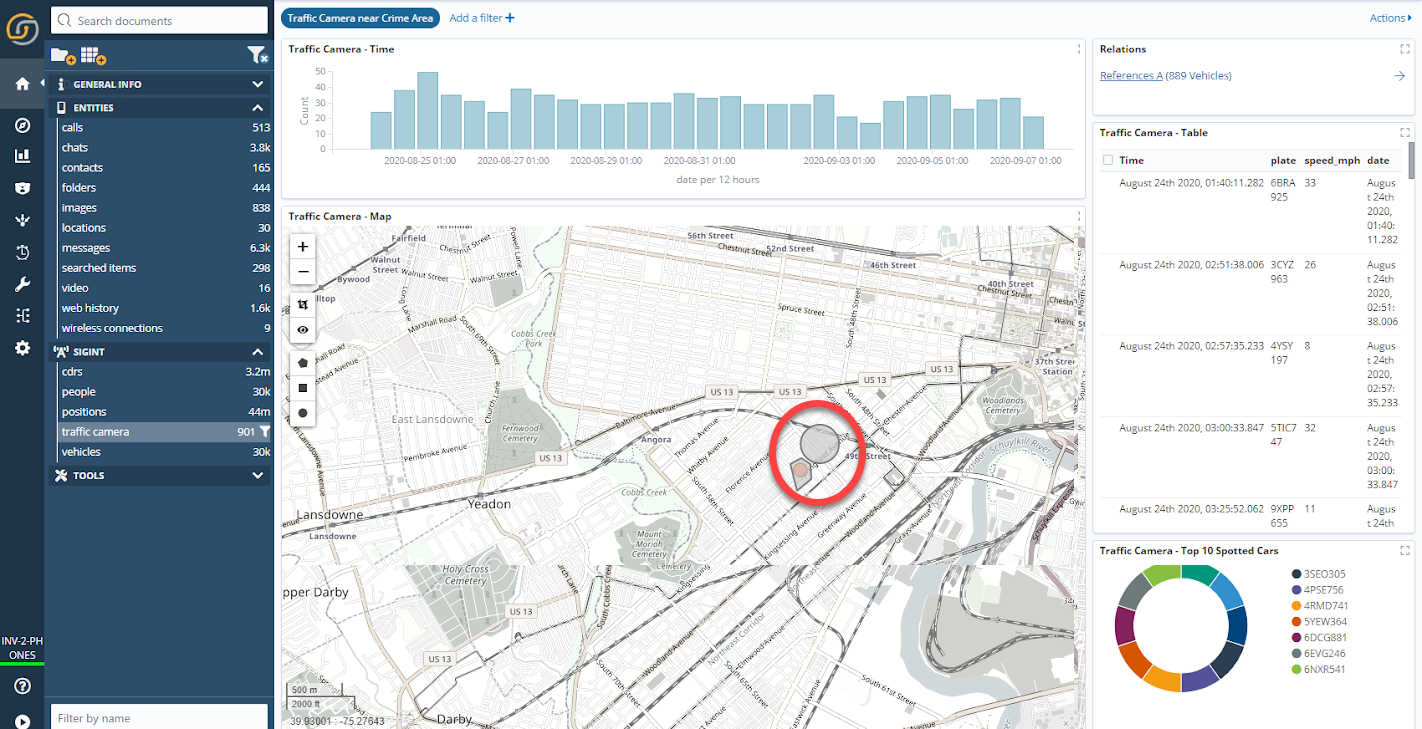
In Siren, one can simply open the dashboards where camera data is streaming, and select the area and time range to drill down on the car license plates to investigate.
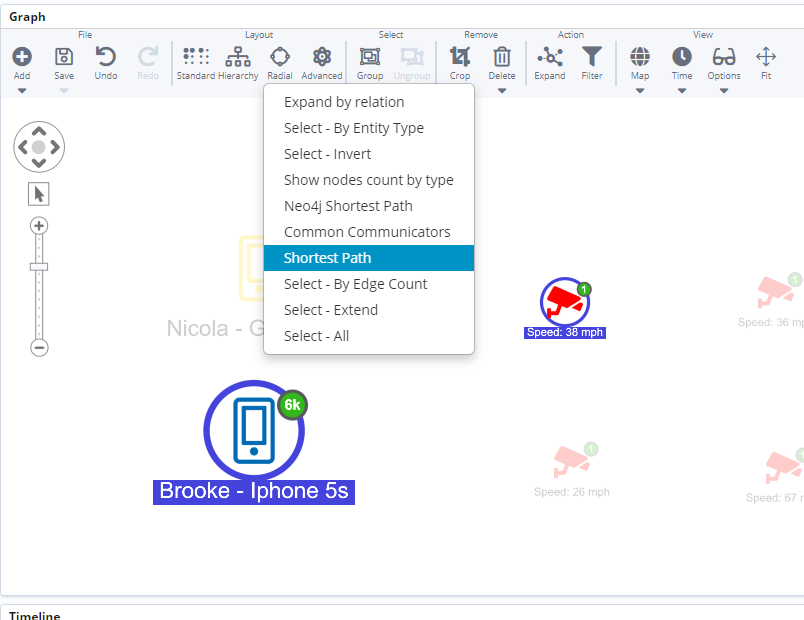
The next task is to find the connection – via any data path – with any of the identifiers extracted from the phone. This can also be done dragging the camera readings in the graph and selecting Shortest Path.
Using the Graph Browser’s Timebar mode, we can easily see that the owner of the confiscated device (Brooke) made a call to Daniel (whose number was saved in Brooke’s contact list) the evening before the attack (24/08/2020 at 8pm). See the image below:
Daniel made a quick call (24 secs) the day after, the 25/08/2020, around 8.45am as reported in the image below:
The callee is the number +12674948782, which belongs to Scott Ford, who also has a car with plate number 5BNG813. That specific car was spotted by the traffic camera (the one close to the attack area) around 9.45am (see image below), just 15 minutes before the attack:
The full path:
Secondly, Siren capabilities are designed to be entity-centric.
The importer is also able to create, on a phone-by-phone basis, a de-duplicated list of parties (the key objects in the XML that represent specific actors involved in calls, messages, etc.) as well as a de-duplicated and curated list of contacts. Some levels of heuristic can be applied to phone numbers to improve in-phone and cross-phone hits.
As opposed to simply “examining the data”, with Siren one can answer questions such as:
- Does a named entity (such as a phone number) have an association to another named entity on the same phone or other phones?
- Can the investigator associate a location stored on a phone to a named entity?
- Does the named entity have association to other data sets such as other subpoena data (CDRs) or structured data such as Law enforcement CAD/RMS
Technical connectors
Technically speaking, the Siren Cellebrite connectors can interact with:
- Cellebrite UFED data dumps in XML formats
- Cellebrite Pathfinder deployments
In either case, the importer can connect and allow the examination of calls, contacts, emails, instant messaging, journeys, social media activity, bookmarks, activity sensors, and many more.
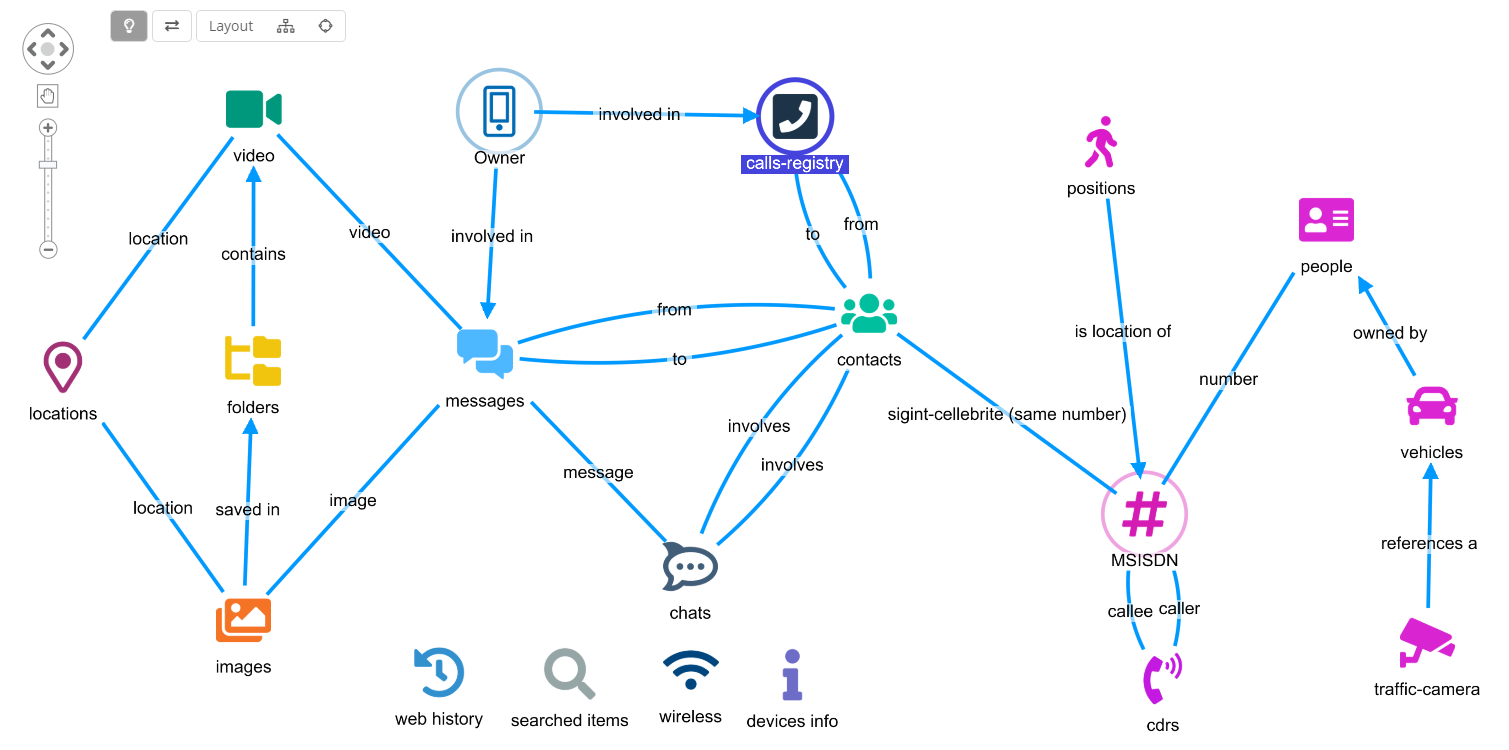
Data is not only extracted but also normalized and properly structured, so it is designed to be easy for the investigator to understand.
.
Conclusions
Siren is committed to protecting people, assets and networks, thanks to a technological approach that is second to none in terms of flexibility in data analysis.
The ease by which Siren version 12 ingests, consolidates and gives access to mobile device data extracted by Cellebrite’s suite of products is testament to this.
What’s more important, however, is that investigators can now avail of the ability to merge, with very little effort, capabilities and datasets that were never easily connected – like the entire content of a mobile device and all the available background data within an organization.
Interested in learning more? Qualifying organizations can reach out and request a demo and a trial. Contact



